In the world of networking, combinations like 172.16.252.214;4300 often appear mysterious to beginners yet are essential for professionals managing internal systems, applications, or secure network communications. This combination of numbers isn’t random—it represents a private IP address paired with a specific port, both critical components of how modern devices communicate. Understanding what each element means helps reveal the structure and purpose behind private network systems and how they function efficiently in everyday digital environments.
Breaking Down 172.16.252.214;4300
To understand the phrase 172.16.252.214;4300, we must separate it into two key elements: the IP address and the port number. The first part, 172.16.252.214, is an IPv4 address, while 4300 represents the port through which data or service communication occurs. Together, they define a pathway within a local or internal network where devices, servers, and applications interact securely and efficiently.
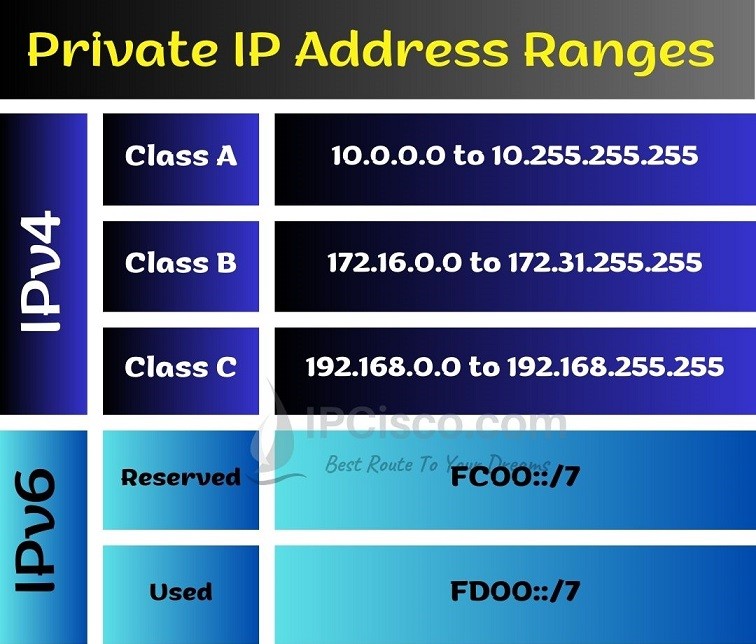
This IP address belongs to the 172.16.0.0 to 172.31.255.255 range, officially reserved for private networks under RFC 1918 standards. That means it’s not accessible over the public internet but instead is used internally within organizations, schools, or large systems for controlled access and communication.
The Role of Private IP Addresses in Networking
Private IP addresses like 172.16.252.214 are the foundation of internal connectivity. They enable multiple devices—computers, printers, routers, and servers—to communicate within the same network without requiring a public IP for each one. This structure not only saves global IP space but also strengthens internal security by isolating the system from external public access.
Enterprises use such IP configurations to manage internal databases, employee access points, and confidential systems that don’t need to interact directly with the internet. By restricting access to the local environment, private IP addresses reduce exposure to external attacks and maintain operational control.
Why the Port Number 4300 Matters
Every port in a network acts like a doorway to a specific service or process. The port number 4300 in the string 172.16.252.214;4300 identifies which type of data exchange is happening. While common ports like 80 or 443 handle web traffic, higher ports such as 4300 are often assigned to custom applications, testing environments, or proprietary communication systems.
Network administrators may configure port 4300 for special software tools, monitoring systems, or even inter-departmental servers. This separation ensures that specific types of data travel through defined and secure routes, avoiding interference with other network processes.
Communication Flow: IP and Port Together
When a system connects to 172.16.252.214;4300, it’s essentially telling the device, “communicate with this specific address and use this particular port.” The IP locates the target device, while the port tells the network which service or program should handle the communication.
For example, within a corporate network, 172.16.252.214 might represent a local file server, and port 4300 could be configured for an internal backup service. Only devices within the same private subnet could access it, ensuring privacy and reducing the risk of external intrusion.
This mechanism is what allows multiple services to operate on a single machine without confusion—each service simply uses a unique port to receive and send data.
Security and Access Considerations
While private IPs are naturally safer than public ones, they still require proper configuration. Firewalls and access control lists (ACLs) are crucial for ensuring that only authorized devices can communicate with addresses like 172.16.252.214;4300.
Administrators often pair such configurations with VPNs or internal DNS management systems to make communication seamless but controlled. If incorrectly set up, even a private IP could expose sensitive internal services to potential misuse, especially if remote access or tunneling is involved.
Regular audits, port management, and encryption protocols help maintain the integrity and confidentiality of such internal setups. In environments where compliance and data protection are top priorities, even private addresses are logged and monitored continuously.
Practical Uses of 172.16.252.214;4300 in Real Environments
Configurations like 172.16.252.214;4300 are often found in:
-
Enterprise intranets, where internal services operate without internet exposure.
-
Development environments, where programmers test applications before deployment.
-
Server clusters, using custom ports for load balancing or data synchronization.
-
Automation systems, linking different modules securely via predefined communication channels.
Such setups demonstrate the hidden backbone of internal IT infrastructure—efficient, secure, and purpose-driven communication inside private networks.
Conclusion
The identifier 172.16.252.214;4300 may look like a technical string, but it represents a vital concept in modern networking: secure, private, and efficient internal communication. The IP defines the device, and the port defines the service. Together, they ensure precise, protected data exchange across local networks.
Whether you’re managing servers, designing secure infrastructures, or studying networking, understanding how private IPs and ports function gives you deeper insight into how digital ecosystems truly operate.